In the ever evolving landscape of cybersecurity, scanning techniques play a crucial role in identifying vulnerabilities, mapping networks, and ensuring the integrity of systems. These methods are essential tools for both defenders, who aim to secure their infrastructure, and potential attackers, who might exploit weaknesses. Below, we explore the various types of scanning techniques, complete with examples, to provide a comprehensive understanding of their purposes and applications.

Port Scanning
Port scanning is a fundamental technique that involves probing a server or host to identify open ports. Open ports can indicate accessible network services, which might be entry points for unauthorized access.
Example: Using a tool like Nmap, a security professional might run nmap -sS 192.168.1.1 to perform a stealth scan on a server, revealing that ports 80 (HTTP) and 443 (HTTPS) are open, suggesting active web services.
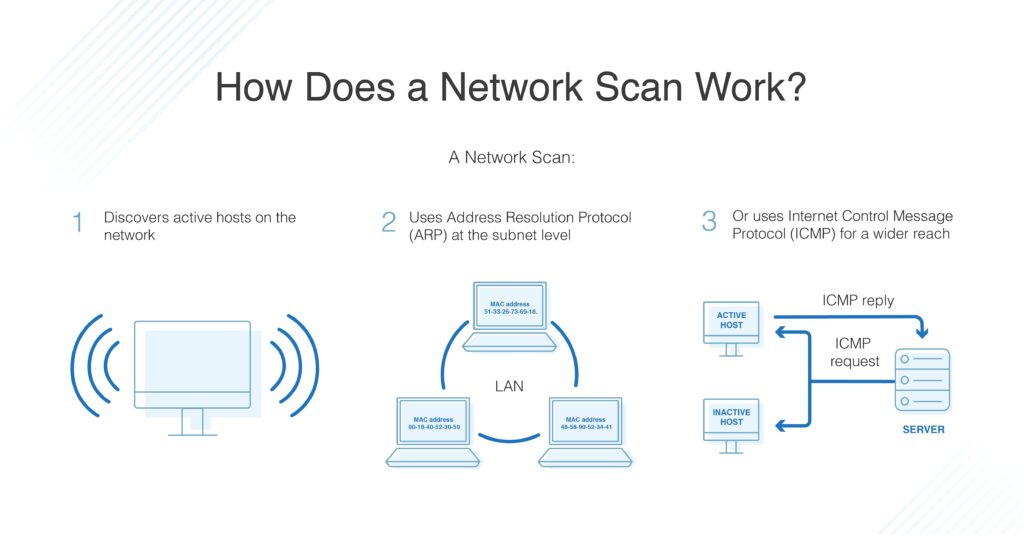
Network Scanning
Network scanning focuses on identifying active devices on a network along with their specific IP addresses. This process helps in creating a map of the network, revealing all connected devices and their configurations.
Example: With a tool like Angry IP Scanner, an admin might scan a subnet (e.g., 192.168.1.0/24) and discover 15 active devices, including printers and workstations, aiding in network monitoring.
Vulnerability Scanning
Vulnerability scanning employs specialized tools to detect security weaknesses in systems and network infrastructures. These scanners analyze software, configurations, and other components to identify known vulnerabilities.
Example: Running Nessus on a corporate server might flag an unpatched Apache server (version 2.4.18) with a known CVE-2017-5638 vulnerability, prompting immediate patching.
OS Fingerprinting
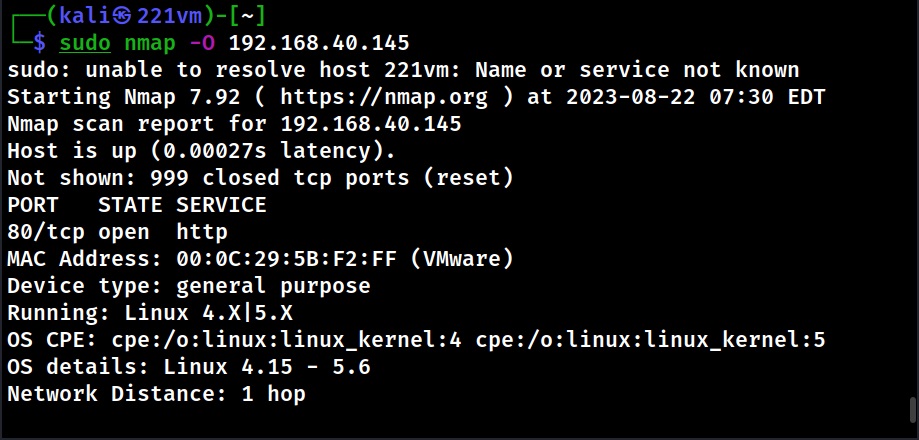
Operating System (OS) fingerprinting is a technique used to determine the operating system running on a remote computer. By analyzing the characteristics of the network traffic or responses from the target system, security experts can identify the OS version.
Example: Using Nmap with the command nmap -O 192.168.40.145, a scan might identify the target as running Linux or Windows 10 (build 1909), allowing for OS-specific security measures.
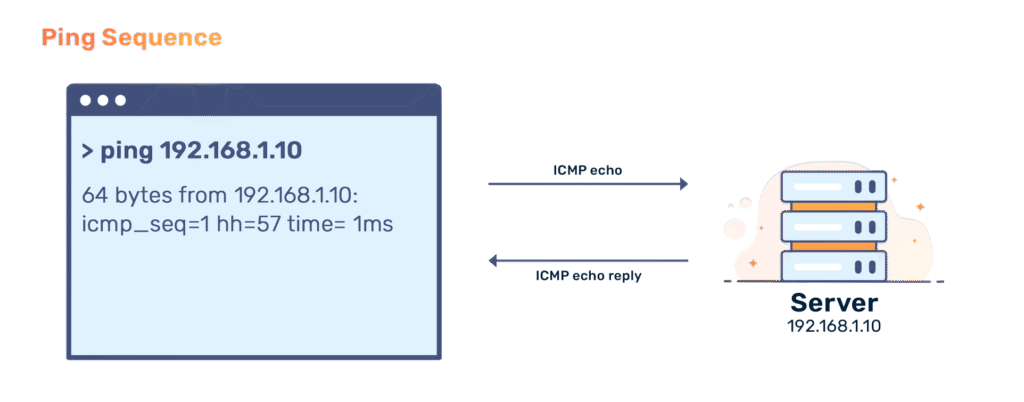
Ping Sweeps
Ping sweeps involve sending Internet Control Message Protocol (ICMP) echo requests to multiple hosts to determine which IP addresses are active. This method is an efficient way to discover live devices on a network.
Example: Executing ping -c 4 192.168.1.1-100 in a terminal might show responses from IP addresses 192.168.1.5, 192.168.1.12, and 192.168.1.25, indicating active devices.
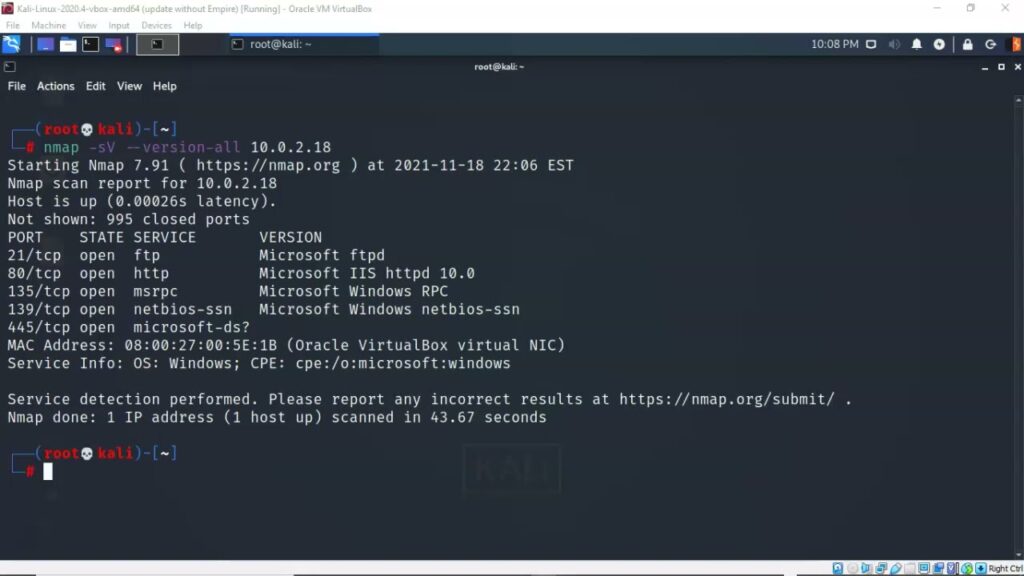
Service Version Scanning
Service version scanning identifies the version of services running on open ports to determine potential vulnerabilities. This technique provides detailed insights into the software and services in use.Example: An Nmap scan with nmap -sV 192.168.1.1 might reveal an SSH service running version 7.4p1 on port 22, which could be cross-checked against known vulnerabilities for that version.
Packet Injection Scanning
Packet injection scanning involves sending custom packets to the network and analyzing the responses to learn about the network’s rules and characteristics. This advanced technique allows security professionals to test how the network handles unusual traffic.
Example: Using a tool like Scapy, a security expert might craft and send a custom TCP packet to port 80 of 192.168.1.1, analyzing the response to detect if the firewall drops or allows the packet, revealing rule configurations.
Conclusion
The diverse range of scanning techniques port scanning, network scanning, vulnerability scanning, OS fingerprinting, ping sweeps, service version scanning, and packet injection scanning, forms the backbone of proactive cybersecurity. Each method, as demonstrated by these examples, serves a unique purpose, from mapping network assets to identifying and mitigating vulnerabilities. By leveraging these tools effectively, organizations can strengthen their defenses and stay one step ahead of potential threats.